

In the landscape of 2026, QR codes have become as commonplace as email, with over 2.9 billion people worldwide expected to use them for everything from payments to accessing information. This widespread adoption, however, has cast a long shadow. The very convenience that makes QR codes so appealing has also made them a prime target for cybercriminals, giving rise to a sophisticated and pervasive threat: quishing, or QR code phishing. As we navigate this new reality, understanding the intricacies of QR code security is essential for both individuals and businesses.
This article provides a comprehensive guide to QR code security in 2026. We will explore the latest threats, dissect the anatomy of a quishing attack, and provide actionable security best practices and compliance requirements to help you navigate the evolving world of QR codes safely and securely.
Once a novelty, QR codes have seamlessly integrated into the fabric of our daily lives, evolving from a niche marketing tool into a piece of essential digital infrastructure. By 2025, over 90% of marketers reported using QR codes, with 94% having increased their usage in the preceding year alone. This signals a lasting transformation in the way we interact with the world around us.
This ubiquity is fueled by staggering user engagement. In 2025, reports indicated that nine in ten consumers engage with a QR code at least once a week, and more than half scan them daily. The global QR code payment market, valued at $14.7 billion in 2024, is projected to surge to $38.2 billion by 2030, underscoring the technology's critical role in the global economy. This deep integration into payments, logistics, and enterprise workflows has raised the stakes for QR code security, making it a paramount concern for businesses and consumers alike.
While QR codes offer immense utility, their proliferation has been accompanied by a significant rise in malicious activity. The primary threat that has emerged is quishing, a portmanteau of "QR code" and "phishing." This form of cyberattack uses a malicious QR code to direct users to a fraudulent website, where their sensitive information, such as login credentials or financial details, can be stolen.
A December 2025 report from cybersecurity firm Kaspersky highlighted the alarming scale of this problem, revealing a fivefold surge in phishing emails containing malicious QR codes during the second half of 2025. The number of detected incidents jumped from 46,969 in August to a staggering 249,723 by November, demonstrating the rapid growth of this attack vector. The U.S. Federal Bureau of Investigation (FBI) has also issued public warnings about the dangers of quishing, noting that cybercriminals are increasingly using this method to perpetrate fraud .
Quishing attacks are effective because they cleverly bypass traditional security measures. Many email filters are not designed to detect malicious URLs hidden within the pixels of a QR code, especially when embedded in a PDF attachment — the most common delivery method. This allows attackers to reach their targets' inboxes with ease. The attack often preys on a user's trust, using social engineering tactics such as fake human resources notifications, fraudulent invoices, or bogus security alerts to create a sense of urgency and trick the user into scanning the code.
To better understand this threat, let's examine the typical stages of a quishing attack.
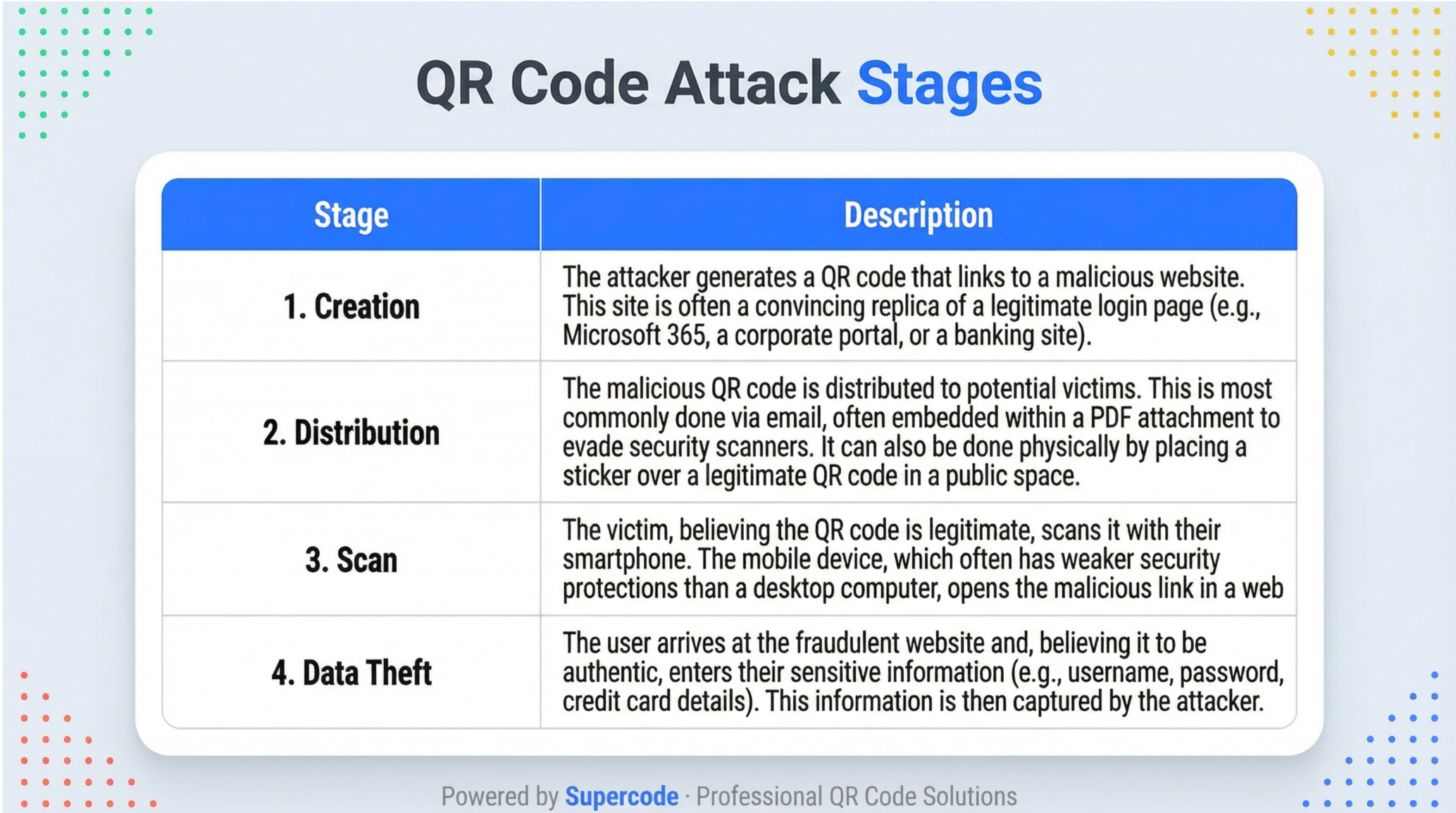
It is a common misconception that QR codes themselves can be "hacked." In reality, a QR code is simply a visual representation of data—a vessel for information. The security of a QR code is not determined by the code itself, but by the destination of the data it holds and the trustworthiness of its creator. This distinction is particularly important when considering the two main types of QR codes: static and dynamic.
Static QR codes are the simplest form of this technology. The destination URL or data is encoded directly into the pixelated pattern. Once generated, a static QR code cannot be altered. While this immutability may seem secure, it carries its own set of risks. If the encoded URL contains a typo, leads to an outdated webpage, or is discovered to be malicious, the QR code is permanently flawed. There is no way to fix it without creating and redistributing a new code, and there is no way to track its usage.
Dynamic QR codes, on the other hand, offer a more flexible and secure alternative. In a dynamic QR code, the code itself contains a short, unique URL that redirects the user to the final destination URL. This intermediate step allows the destination to be changed at any time without altering the QR code itself. This provides significant security advantages, including the ability to correct errors, update links, and track scan analytics. However, this flexibility also introduces a new potential point of failure: if the QR code management platform is compromised, an attacker could potentially hijack the redirect and send users to a malicious site. This underscores a critical point: the security of a dynamic QR code is inextricably linked to the security of the platform used to create and manage it.
For businesses that leverage QR codes for marketing, logistics, or customer engagement, ensuring their security is not just a best practice—it is a business imperative. A single compromised QR code can lead to significant financial loss, reputational damage, and a loss of customer trust. Therefore, a multi-layered defense strategy is essential for any organization deploying QR codes in 2026.
<picture>
This strategy begins with choosing a secure QR code generation platform. When evaluating potential vendors, businesses should look for platforms that can demonstrate a strong commitment to security through both their features and their compliance with industry standards. The following checklist can serve as a guide for this evaluation process:
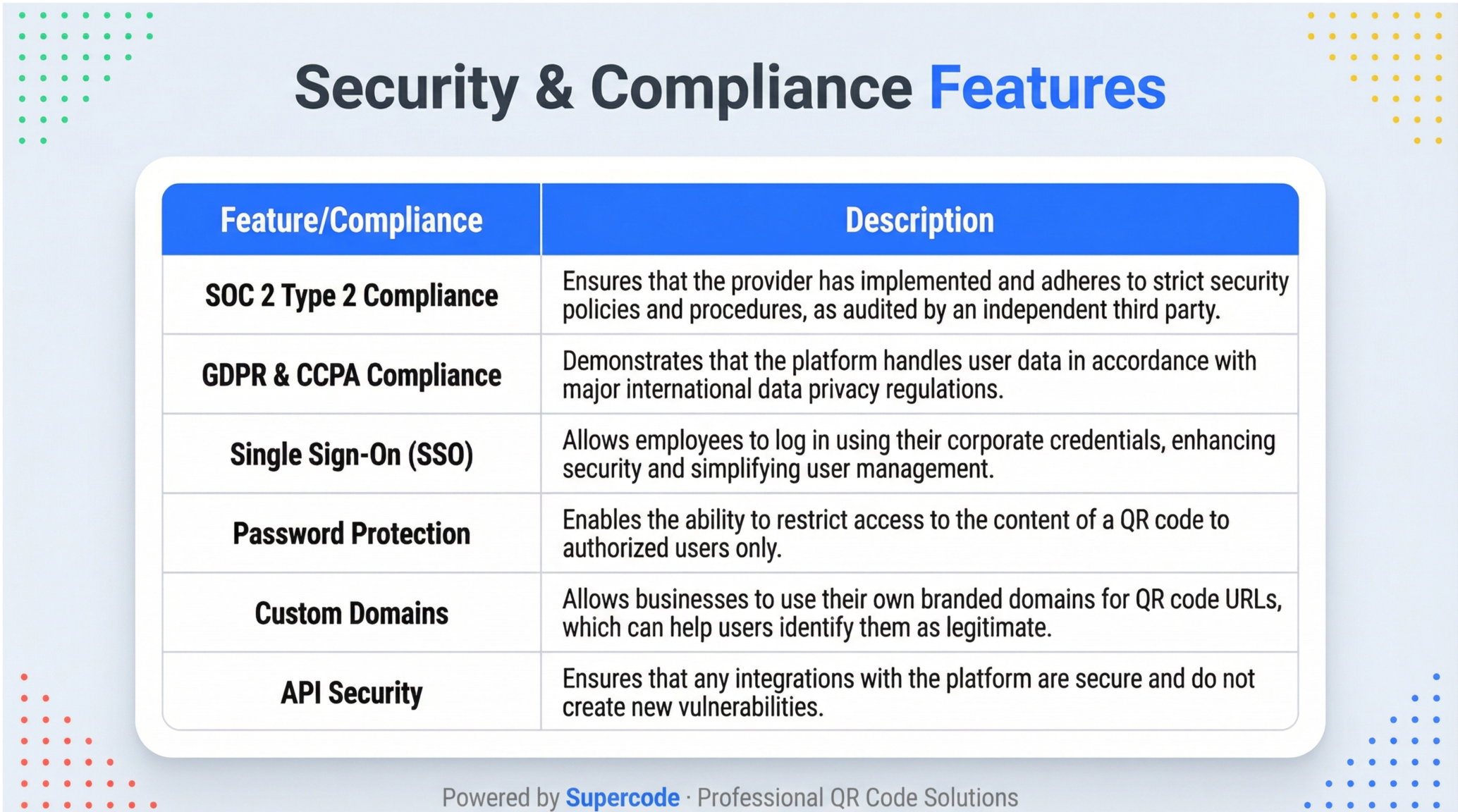
Beyond platform-level security, organizations must also implement robust internal security practices. This includes providing regular training to employees on how to identify and report potential quishing attacks, establishing clear policies for the creation and deployment of QR codes, and equipping company-owned mobile devices with advanced security solutions that can detect and block malicious threats.
Finally, technical security measures, such as implementing email security solutions with advanced image analysis capabilities and adopting zero-trust principles for access to QR code-related systems, can provide an additional layer of defense against the evolving threat landscape.
While businesses bear a significant responsibility for securing the QR codes they create, consumers also play a crucial role in protecting themselves. By adopting a cautious and informed approach to scanning QR codes, individuals can significantly reduce their risk of falling victim to a quishing attack. The following tips can help you scan safely in 2026:
Before You Scan:
• Consider the Context: Before scanning a QR code, take a moment to assess its surroundings. If the code is on a physical object, such as a poster or a parking meter, check to see if it is a sticker that has been placed over another, legitimate code. If the code is in an email, verify that the sender is who they claim to be and that the request to scan the code is expected and makes sense.
• Inspect the URL: Many modern smartphone cameras will show you a preview of the URL embedded in a QR code before you open it. Take a moment to inspect this URL. Look for red flags such as the use of a URL shortener (like bit.ly), misspellings of familiar brand names, or the use of an HTTP connection instead of the more secure HTTPS.
After You Scan:
• Be Wary of Login Pages: If a QR code takes you to a page that asks for your login credentials, be extremely cautious. It is very rare for a legitimate company to ask you to log in to your account via a QR code. When in doubt, close the page and navigate to the company's website directly through your browser.
• Protect Your Personal Information: Never enter sensitive personal information, such as your credit card number or social security number, on a website you have accessed via a QR code unless you are absolutely certain that the site is legitimate and secure.
The fight against QR code-related cybercrime is an ongoing battle, but new technologies are emerging that promise to make QR codes even more secure. In the coming years, we can expect to see the wider adoption of AI-powered threat detection systems that can identify and block malicious QR codes in real time. Blockchain technology also holds promise for creating a decentralized and immutable ledger of QR codes, making it much more difficult for attackers to tamper with them. Finally, the integration of biometric authentication, such as fingerprint or facial recognition, could add an additional layer of security to QR code scans, ensuring that only authorized users can access the content they contain.
QR codes have firmly established themselves as an indispensable tool in our increasingly digital world. Their convenience and versatility are undeniable, but so are the security risks that have accompanied their rise. The threat of quishing is real and growing, and it requires a concerted effort from both businesses and individuals to combat it effectively.
By choosing secure and compliant QR code platforms, implementing robust internal security practices, and fostering a culture of awareness and caution, we can continue to benefit from the many advantages of QR codes while minimizing the risks. In the landscape of 2026, safe QR code usage is a shared responsibility, and it is one that we must all take seriously.
For businesses looking to create secure, reliable, and manageable QR codes, a trusted platform is the first and most important line of defense. Supercode offers a secure, enterprise-grade QR code generator that is SOC 2 Type 2 compliant and provides all the features you need to protect your business and your customers.

Q: What is quishing?
Quishing is a type of phishing attack that uses a malicious QR code to trick users into visiting a fraudulent website and revealing their sensitive information.
Q: Can my phone get a virus from a QR code?
While it is technically possible for a QR code to lead to a website that attempts to download malware to your phone, it is a relatively rare occurrence. The more common threat is phishing, where the goal is to steal your credentials rather than infect your device.
Q: How do I know if a QR code is safe?
There is no foolproof way to know for sure, but you can look for red flags suchas a suspicious URL preview, a physical sticker that appears to be covering another code, or an unexpected request to scan a code in an email. When in doubt, it is always best to err on the side of caution and not scan the code.
Q: Are payment QR codes secure?
Payment QR codes from reputable providers are generally very secure. They use encryption and other security measures to protect your financial information. However, you should always be cautious and make sure that you are using a legitimate payment app and that the QR code has not been tampered with.
Q: What is a dynamic QR code?
A dynamic QR code is a type of QR code that uses a short redirect URL, allowing the destination of the code to be changed without altering the code itself. This makes them more flexible and secure than static QR codes.
Q: What is the difference between a static and a dynamic QR code?
A static QR code contains the final destination data directly, while a dynamic QR code contains a link to a server that then redirects the user to the final destination. This means that dynamic QR codes can be edited and tracked, while static QR codes cannot.
Q: Can QR codes be hacked?
The QR code itself cannot be hacked, but the destination it leads to can be malicious. The security of a QR code depends on the trustworthiness of its creator and the security of the platform used to manage it.
Q: What is SOC 2 compliance and why is it important for QR code generators?
SOC 2 is a set of standards for managing customer data based on five “trust service principles”—security, availability, processing integrity, confidentiality, and privacy. A SOC 2 compliant QR code generator has been audited by a third party and has been shown to have robust security controls in place.
Q: What is GDPR and how does it apply to QR codes?
The General Data Protection Regulation (GDPR) is a European Union law that governs data protection and privacy. If a QR code is used to collect any personal data from individuals in the EU, the company that created the code must comply with GDPR.
Q: What is CCPA and how does it apply to QR codes?
The California Consumer Privacy Act (CCPA) is a California state law that gives consumers more control over the personal information that businesses collect about them. Like GDPR, it applies to any company that collects personal data from California residents via QR codes.
Q: How can I protect my business from quishing attacks?
The best way to protect your business is to use a secure, enterprise-grade QR code generator, train your employees to recognize and report phishing attempts, and implement a multi-layered security strategy that includes both technical and policy-based controls.
Q: What should I do if I think I have scanned a malicious QR code?
If you think you may have scanned a malicious QR code, you should immediately close the browser window, clear your browser's cache and cookies, and change the password for any accounts you may have accessed.
Q: Are free QR code generators safe?
Many free QR code generators do not offer the same level of security and features as paid platforms. They may not be compliant with data privacy regulations, and they may not offer features like password protection or custom domains. For businesses, it is always recommended to use a reputable, paid platform.
Q: Can a QR code track my location?
A QR code itself cannot track your location. However, if you scan a QR code that takes you to a website, that website may ask for your permission to access your location data.
Q: What are some of the benefits of using dynamic QR codes?
Dynamic QR codes are editable, trackable, and more secure than static QR codes. They allow you to change the destination URL at any time, track the number of scans, and gather valuable data about your users.
Q: How are QR codes used in marketing?
QR codes are used in marketing to bridge the gap between the physical and digital worlds. They can be used to direct users to a website, a social media page, a video, or a special offer. They can also be used to track the effectiveness of marketing campaigns.
Q: What is a QR code payment?
A QR code payment is a type of contactless payment where you scan a QR code with your smartphone to pay for goods or services. It is a fast, convenient, and secure way to make payments.
Q: Are QR codes still relevant in 2026?
Yes, QR codes are more relevant than ever. They are used in a wide variety of applications, from payments and marketing to logistics and healthcare. Their usage is expected to continue to grow in the coming years.
Q: What is the future of QR codes?
The future of QR codes is likely to involve even greater integration with other technologies, such as augmented reality and the Internet of Things. We can also expect to see continued advancements in QR code security.
Q: Where can I create a secure QR code?
For the highest level of security and compliance, it is recommended to use an enterprise-grade QR code generator like Supercode. Supercode is SOC 2 Type 2 compliant and offers a wide range of security features to protect your business and your customers.
Try Supercode QR code generator for secure QR codes every time.